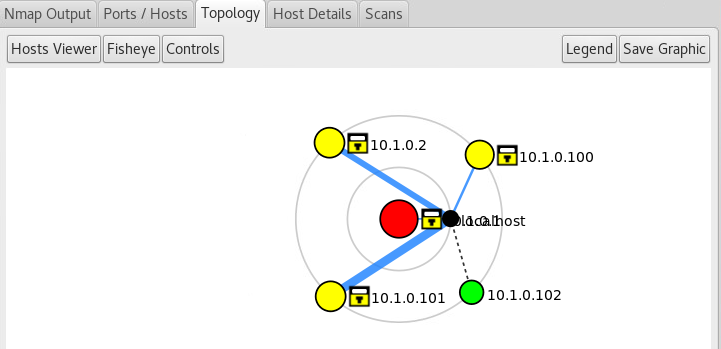
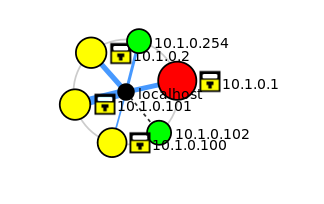
A VPN is a Virtual Private Network.
Its a way of allowing a remote user to access a network over an untrusted public connection, i.e. the internet. An employee can work from home or any other location and still access their data and app from the network.
The importance of the VPN is to provide a secure connection, such that the data cannot be intercepted or modified. So the VPN must provide for encryption.
We also need a secure encrypted authentication method to allow authorised users to get in.
1 – Configure a RADIUS Server and Client
Remote Authentication Dial-In User Service (RADIUS) is an authentication and access protocol developed to allow centralised access to a network. A simple example would be a user entering a network via a router, the router acts as a RADIUS server and will authenticate with the AD.
In Server2016 the equivalent is a Network Policy Server.
The pfSense firewall will also function as a router and a RADIUS server.

I realised here that copy and paste will not work on the VM, so I choose a shorter memorable manual shared secret, not best-practice but at least I will not need to type the auto generated secret shown above and no doubt have numerous typos.
The network policy wizard the sets the policies for VPN access, here we can configure settings such as time of day access.

The firewall is now a RADIUS server, note my smaller manual shared secret.
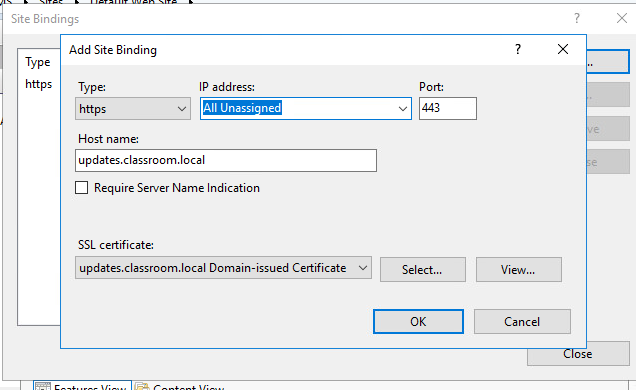
2 – Configuring the VPN concentrator
IKEv2 – refers to Internet Key Exchange
VPN concentrator is a router that allows multiple secure connections into a network.
First a Certificate Authority on the firewall.

And next created a certificate.
IPSEC tunnels was set firstly to share a key and secondly to negotiate the encryption protocols to be used by the connection, the data through the “tunnel” will be encrypted and the client machine needs to know which encryption to use.
3- The Client Configuration
In this exercise a GPO is used to configure the clients, this can then be applied to all the computers in the domain, no need to individually set the clients.
First we trust the certificate we issued from pfSense.
Then we set a GPO for network options which connects via our firewall ip address and requires an authentication protocol for security.
Before configuring the options for the clients IPv4 connection properties, I had to do a gpupdate /force on the Win10 machine, it hadn’t received the GPO which created the Classroom VPN adapter.

4 – Connecting to the VPN
It will be interesting to see if this works!

2 hours of work later, and no luck. I am going to have to redo the lab and check my configurations!
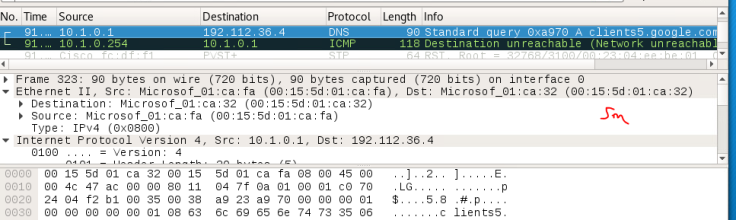
But first, can I ping the 10.1.0.0 network, I created a firewall rule to allow ICMP requests through the firewall, and one ping storm later and I can ping all the way from the 192.168.0.0 network to the DC, so the connection to the network is functional.
Update: I had a conversation with a colleague in my class, he’s a bright guy and we have kept up with each others progress through the Labs, so we are likely the only 2 working on this Lab. He has exactly the same problem and same error as me. This is highly suggestive of a problem with the Lab rather than a PEBKAC (problem exists between chair and keyboard).
We’ll keep an eye on the forum for the course and see if anyone fixes this bug.
Update 09/10 ex 2: I had my tutor look at my Lab and have discovered an error in the ex 2 where a tab in the firewall wasn’t available to set a rule to allow IPSec requests through the firewall, after re-doing the Lab this option is now available, so lets see if this is a fix.


The firewall should now allow IPSec requests through.
So I redid all the Lab and also used the fixes suggested by colleagues, but I am unable to authenticate a user in the Pfsense, despite applying all the fixes as suggested by them. So still no connection through the VPN.
So one fix sorted but still not connecting.
An extreme exercise in patience and managing frustration, despite multiple attempts at this Lab and following all the fixes supplied by colleagues, I still can’t get a VPN connection on the network.
Critical Thinking
These Labs were an interesting learning experience, they offer a great look into the world of Network security and allowed us to experience many tools that are available both to protect and monitor networks.
Interestingly, the same tools are used by the very people we are protecting our network from. We can use the same tools to either attack or defend a network.
The most valuable experience came from the actual doing of the Labs, we used a different virtual environment (VSphere VMs) from the environment the Lab was built to run on (VMWare) and this through in many technical challenges to get the Labs to work.
Some were smooth and painless, but others especially Lab 12 was a massive challenge to set up the initial network just to get a “ping” request to travel across from one network to another.
The majority of the class have benefited from the tutors input here, a select few of us completed this Lab by building the network and ironing out the bugs which we have posted in forum posts to benefit the others. The tutor also fixed a lot of the settings to make the Lab setup a lot simpler. No worries, I learnt a huge amount from this Lab in particular about my abilities to problem solve an issue.
A second issue I have learned is about testing. These Labs were designed and written by people and not surprisingly there are errors in the Lab, some are just simple typos in the document. But I think for the price we paid for this course that the sellers of the e-book should have tested the course in a real virtual environment, this could have avoided a lot of the simple errors we had to problem solve. Reminder to myself, test everything, ideally by someone not involved in the design and build of a system.
Since we bought the e-textbook for this course, things have changed and the price of the textbook has doubled. Feedback from our tutor who has not used this version of the course before, suggests that the next version of this course will drop these Labs as just too expensive now for the average student.




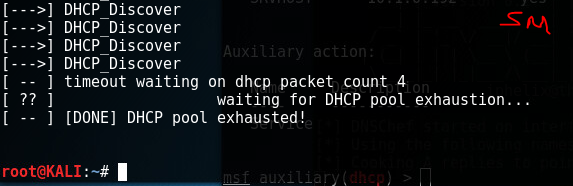
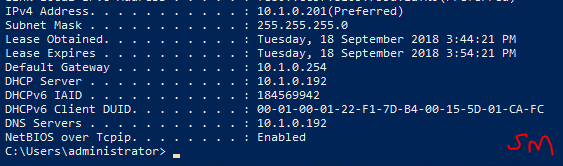





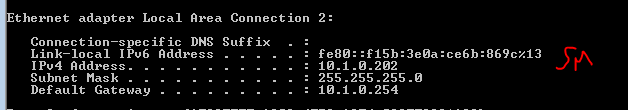




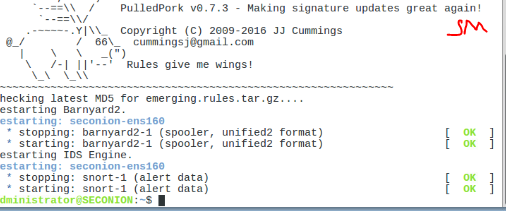


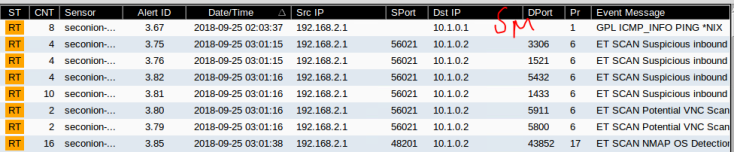






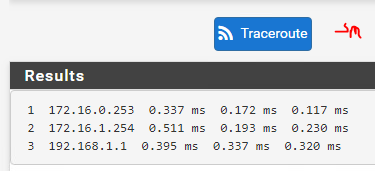
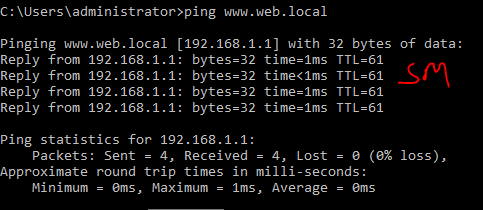
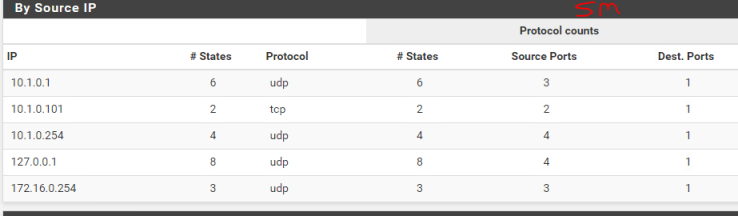
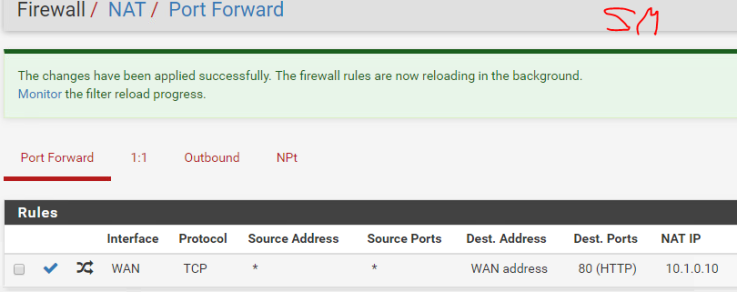
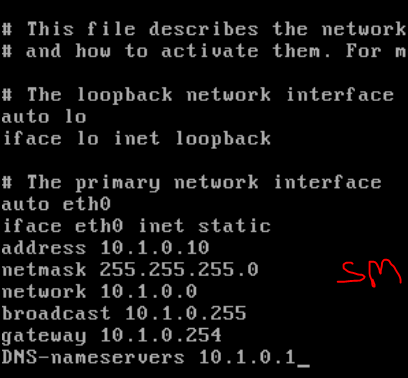
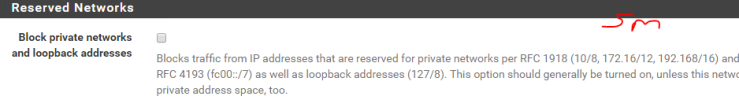

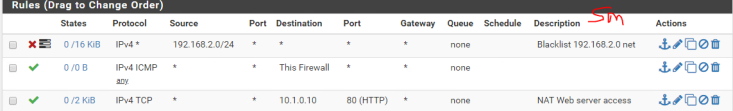

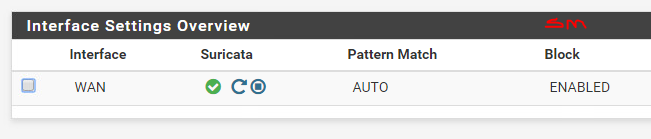


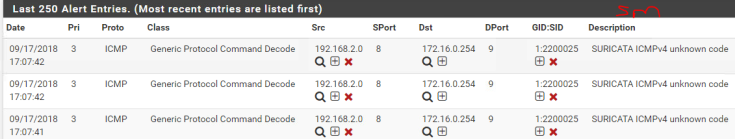

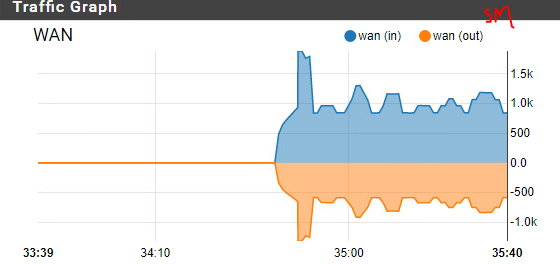


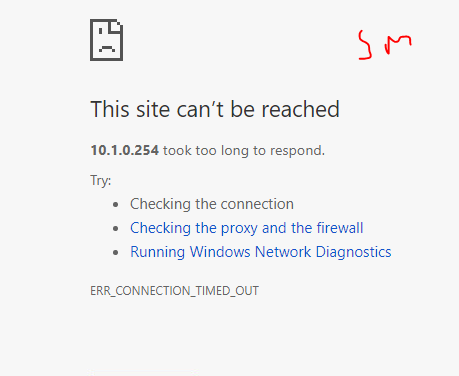
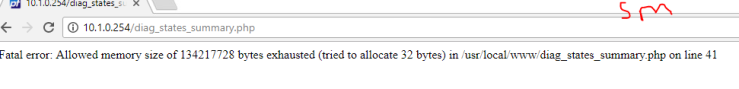
 Interesting exercise, a firewall is designed in such a way as to detect DoS attacks, unfortunately this little hping3 masquerades as coming from random sources and the firewall does realize its being attacked.
Interesting exercise, a firewall is designed in such a way as to detect DoS attacks, unfortunately this little hping3 masquerades as coming from random sources and the firewall does realize its being attacked.